Brute force…sort of.
Initially I was checking for security vulnerabilities and stumbled across this. By gaining access to the the UDP-based RSTP stream that contains actual camera footage I was able to redirect it to my media server. I wrote an article on this but its based more on the vulnerability than the local storage work around.
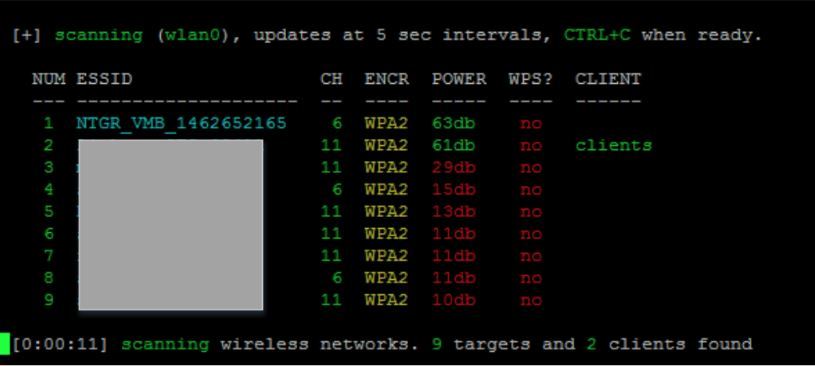
An open source boot manager based on modified linux that requires no credentials to login allowing easy root access through BusyBox. When exploring you will find that when a factory reset is performed on system the default passphrase becomes 12345678 and a “random” SSID in the format “NTGR_VMB_<10 digit numbers>“.
loaddefault finished
Passphrase – 12345678
BurnPassphrase OK
SSID – NTGR_VMB_1462245431
BurnSSID OK
This operation is performed by an executable that is run on the system by default “/bin/vzdaemon”. The following disassembly shows the routine performs the passphrase and SSID reset operation – the SSID reset is based upon the current date and time of the systemAfter the factory reset, you can confirm that the wpa_psk and other values are reset to the default 12345678 string.
# nvram show|grep 12345
size: 25206 bytes (40330 left)
wl_wpa_psk=12345678
wl0_wpa_psk=12345678
wla_preset_passphrase=12345678
wla_passphrase=12345678
Then join the network
As you know the passphrase for this network, after collecting Wi-Fi packets from this network, decrypt the traffic to an unencrypted state which contained various JSON traffic between the base station and ARLO cameras. Beyond this basic communications traffic, capture RTSP traffic – this is a protocol that carries the images and video stream from the ARLO cameras.
To perform this Wi-Fi packet decryption, you need to capture Wi-Fi packets using monitoring mode. After that, generate PSK string using the wpa_passphrase tool from Linux. With the Wi-Fi packet dumps opened from Wireshark, select Edit -> Preferences -> Protocols -> IEEE 802.11 -> Edit menu and add the PSK generated from the previous command. With the Wi-Fi packet dumps opened from Wireshark, select Edit -> Preferences -> Protocols -> IEEE 802.11 -> Edit menu and add the PSK generated from the previous command. That will allow you to see the unencrypted connections between cameras and base. You will see various JSON traffic data, but on destination port 554 of the cameras, the base station actually sends RTSP requests.
From the RTSP protocol session, identify the UDP-based RSTP stream that contains actual camera footage, use example
SETUP rtsp://172.14.1.101/live/track1 RTSP/1.0
CSeq: 3
Transport: RTP/AVP;unicast;client_port=1038-1039
If-Modified-Since: Thu, 01 Jan 1970 00:00:00 GMT
RTSP/1.0 200 OK
CSeq: 3
Server: NgcRtspService/1.0
Date: Tue, Jul 16 2014 20:10:37 GMT
Transport: RTP/AVP/UDP;unicast;client_port=1038-1039;server_port=9418-
419;ssrc=1766339330;mode=play
Session: 1103527590;timeout=60
Content-Length: 0
From the list from UDP RTP sessions locate the matching session. Each UDP packets are sending RTP packets using standard RTP format.

I found that there is no easy or straightforward way to convert Wireshark PCAP data to a video file (MP4 file) and wrote a simple python script that functions as an RTSP and RTP server.
If I missed something let me know, that was a lot to write on my phone